DPDPA Compliance and Cybersecurity Ecosystems


Author:
Sairaj Mahesh, CEO – WorldStartupNews
Abstract
The enforcement of the Digital Personal Data Protection Act (DPDPA) in India represents a critical juncture in the nation’s digital governance landscape. The Act establishes comprehensive obligations for organizations collecting, processing, and safeguarding personal data, aligning India more closely with international regimes such as the EU’s GDPR. This article provides an analytical exploration of the DPDPA through the lens of industry practices and technologies. Drawing on insights from the DPO Club event and discussions with management teams of TÜV SÜD, OneTrust, GoTrust, Strobes, Qualys, Security Brigade (ShadowMap), and Tenable, this study examines how cybersecurity audits, privacy governance platforms, vulnerability management systems, and exposure monitoring tools collectively form a compliance ecosystem. The analysis demonstrates that successful DPDPA implementation requires a hybrid approach—combining governance frameworks with security technologies to ensure both legal accountability and operational resilience.
Keywords: DPDPA, Data Protection, Cybersecurity, Privacy Governance, Vulnerability Management, Compliance Ecosystem
1. Introduction
The year 2023 marked a turning point in India’s legislative journey toward a privacy-first economy with the introduction of the Digital Personal Data Protection Act (DPDPA). Unlike fragmented data protection guidelines of the past, the DPDPA introduces an integrated framework that governs personal data collection, processing, storage, and transfer. The law places significant responsibilities on organizations, termed “data fiduciaries,” while granting enhanced rights to individuals, known as “data principals.”
India’s Digital Personal Data Protection Act (DPDPA) marks a historic shift in how organizations must collect, process, and protect personal data. For Indian companies, compliance is no longer optionalit is a mandate backed by penalties, reputational risk, and regulatory oversight.
But compliance is not just about ticking legal boxes. It requires a strong mix of privacy governance, security controls, audits, and continuous monitoring. This is where leading global and Indian cybersecurity vendors step in.
The globalization of data governance has compelled Indian enterprises to adapt. International stakeholders increasingly demand parity with global frameworks like the General Data Protection Regulation (GDPR) (Voigt & Von dem Bussche, 2017). Therefore, DPDPA compliance is not only a statutory requirement but also a business differentiator for Indian firms aiming to compete globally.
During my participation at the DPO Club event, I interacted with stakeholders from leading cybersecurity solution providers. These conversations revealed how tools and services from TÜV SÜD, OneTrust, GoTrust, Strobes, Qualys, Security Brigade’s ShadowMap, and Tenable align with the DPDPA’s compliance and operationalization challenges. This article extends those insights into a structured analysis, presenting an industry-oriented journal-style contribution.
2. The Digital Personal Data Protection Act: An Overview
2.1 Objectives of the Act
The DPDPA aims to:
-
Establish a legal framework for personal data in India.
-
Grant individuals rights such as access, correction, and erasure of their personal data.
-
Impose obligations on data fiduciaries to collect only necessary data and ensure security safeguards.
-
Mandate breach notification within specified timelines.
2.2 Key Principles
Scholarly literature on privacy frameworks emphasizes data minimization, purpose limitation, accountability, and transparency as cornerstones (Solove, 2020). The DPDPA echoes these principles while contextualizing them for India’s digital economy.
2.3 Compliance Challenges
Indian organizations face multiple challenges:
-
Mapping vast and unstructured data landscapes.
-
Aligning legacy IT systems with new obligations.
-
Building consumer trust in a market where digital breaches frequently dominate headlines (PwC India, 2023).
These challenges necessitate the integration of audit expertise and technological solutions, forming what I term a compliance ecosystem.
1. TÜV SÜD — Audits, Certifications, Trust & Cybersecurity Assurance

What they offer
-
TÜV SÜD is a global technical services firm offering auditing, certification, and advisory services in cybersecurity and data protection.
-
In India, TÜV SÜD is empanelled by CERT-In (Indian Computer Emergency Response Team) to perform cybersecurity audits and regulatory compliance assessments.
-
They also run data protection and privacy audits (gap assessments), help establish data governance frameworks, and can certify to standards like ISO 27701 (Privacy Information Management System) as an extension of ISO 27001.
-
TÜV SÜD specifically markets a “Digital Personal Data Protection Compliance” service in India, helping organizations map, classify, safeguard data, respond to data subject rights, and maintain continuous compliance. TÜV SÜD
How this helps Indian firms under DPDPA / DPDP
-
Third-party credibility: A certification or audit by a recognized independent body adds legitimacy to a company’s privacy posture. It helps build trust with customers, regulators, and partners.
-
Gap analysis and roadmap: Many firms may not yet be ready for DPDPA. TÜV SÜD’s audits help them identify where they fall short (e.g. in data minimization, retention, access controls) and plan remediation.
-
Regulator readiness & defence: In case of enforcement or scrutiny, having undergone formal audits or certification can strengthen the firm’s defense (i.e., show due diligence).
-
Standard alignment: Using ISO 27701 or equivalent frameworks helps Indian firms align with global best practices (e.g. GDPR, others), making cross-border operations smoother.
-
Ongoing assurance: TÜV SÜD can do periodic surveillance audits, continuous compliance validation, training, and policy updates, which is vital given that DPDPA will require evolving technical and organizational measures.
In short, TÜV SÜD can serve as a compliance anchor, offering audit, certification, and advisory support to help Indian firms steer safely through DPDPA obligations.
2. GoTrust & OneTrust — Privacy / Governance / Consent / Risk Platforms
Before going deeper, a clarification: The name GoTrust is less widely covered in public sources; but I assume you refer to a privacy / trust / governance technology company.
The better-known vendor is OneTrust, which is a leading privacy, governance, and compliance software platform. I’ll focus more on OneTrust
What OneTrust offers
-
OneTrust is a comprehensive privacy and governance platform supporting modules for consent & preference management, data use governance, privacy operations, AI governance, vendor risk, and more.
-
OneTrust also integrates with vulnerability / security tools. For example, it can integrate with Tenable to bring vulnerability or web app scanning data into its risk dashboards.
-
OneTrust’s modules help centralize privacy program workflows: data inventory, DPIAs (Data Protection Impact Assessments), subject access request (SAR) handling, assessments, policy management, and compliance reporting.
How this helps Indian firms under DPDPA / DPDP
-
Consent & transparency compliance: DPDPA requires clear consent paths, rights of correction/deletion, and transparency. OneTrust’s consent & preference engine can automate capturing, storing, and managing consents across digital touchpoints.
-
Data mapping / inventory: The Act mandates that firms know what personal data they collect, how they process it, retention, third-party transfers, etc. OneTrust helps maintain inventory and data flow maps.
-
Rights management: It can handle subject rights (access, correction, erasure) requests end-to-end—including tracking, workflows, and audit trails.
-
Risk scoring & compliance dashboards: It allows governance teams to see which business units are at highest risk of non-compliance or violations, aiding prioritization.
-
Integration with security tools: Because OneTrust can link with tools like vulnerability scanners, it helps tie privacy risk with security risk, giving a more unified view of exposures.
-
Policy consistency & updates: OneTrust helps enforce consistent privacy policies, version control, tracking changes, and ensuring that changes to laws (or DPDPA clarifications) are propagated.
If “GoTrust” is a regional/local tool filling similar gaps (consent, trust, privacy operations), combining it with OneTrust or using them together could give Indian firms better localized compliance and scale.
3. Strobes & Qualys — Vulnerability & Exposure Management, Smart Remediation
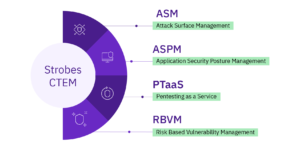
What they are / offer
-
Qualys is a well-known vulnerability scanning, asset discovery, web application scanning, and compliance scanning platform. It helps detect configuration, patching, and vulnerability issues across networks, applications, and cloud infrastructure.
-
Strobes offers a Continuous Threat Exposure Management (CTEM) platform that ingests vulnerability data from scanners like Qualys, correlates them, enriches with context, deduplicates, adds risk prioritization, and automates remediation workflows. Strobes Security
-
The Qualys–Strobes integration is explicitly marketed: Qualys feeds alerts and scan data into Strobes, which filters and prioritizes the most business-critical issues, automates ticketing, and reduces noise. Strobes Security
How this helps Indian firms under DPDPA / DPDP
-
Security as foundation of privacy: The DPDPA will require implementing technical safeguards to protect personal data (encryption, access controls, patching, vulnerability management). Detecting and remediating vulnerabilities is a core requirement.
-
Efficient use of resources: Many organizations get overwhelmed by raw vulnerability output (“too many alerts”). Strobes helps convert that into prioritized, meaningful tasks, reducing alert fatigue and focusing resources on the top 5–10 % of issues that matter most.
-
Automated workflows & accountability: Through integration with ticketing tools (e.g., JIRA, ServiceNow), Strobes ensures that findings are assigned, tracked, and validated post-remediation—helpful for internal audit and compliance evidence.
-
Contextual risk view: Because Strobes enriches vulnerabilities with business context, exploitability data, asset criticality, etc., Indian companies can more defensibly choose what to patch first—aligning with the “reasonable security” standard in DPDPA.
-
Scalable scanning & coverage: Qualys’s wide scanning capabilities ensure that Indian firms get broad visibility into internal, external, cloud, network, and web-based vulnerabilities.
-
Continuous posture improvement: Over time, using this duo helps firms mature their vulnerability management programs, trending down exposures and improving compliance readiness.
Thus, combining Qualys and Strobes gives Indian firms both detection capabilities and actionable remediation workflows—crucial for meeting DPDPA’s technical requirements.
4. Security Brigade — ShadowMap (Digital Risk / External Exposure Monitoring)
What ShadowMap is

-
ShadowMap (by Security Brigade ) is a digital risk protection / attack-surface / external threat monitoring / continuous exposure platform. ShadowMap+1
-
It scans the surface, deep, and dark web for data leaks, credential dumps, brand impersonation, exposed assets, phishing, and other risk signals.
-
Key capability areas: external attack surface management, dark web monitoring of data leaks, phishing takedown, brand protection, threat intelligence, and exposure scoring.
How this helps Indian firms under DPDPA / DPDP
-
Detect leaked personal data early: Under DPDPA, if a data breach or leak occurs, timely detection is critical. ShadowMap helps firms find unauthorized exposures or leaks even before they are large-scale.
-
Continuous external posture monitoring: Firms may forget or lose track of assets (forgotten domains, developer repositories, S3 buckets). ShadowMap helps map these shadow assets and reduce blind spots.
-
Brand / identity protection: Impersonation attacks or abuse of brand domains can lead to reputational harm, or even phishing attacks jeopardizing personal data. ShadowMap supports takedown and monitoring.
-
Correlate threat intelligence & compliance: By combining external signals with internal security logs, a firm can better understand its threat surface and make decisions about stronger protective controls.
-
Compliance and audit readiness: Being able to show that the firm actively monitors for data exposure across the external web strengthens the compliance posture and demonstrates proactive defense.
-
Incident response enhancement: If ShadowMap detects a credential leak or exposure, the firm can mobilize response teams quicker, helping limit the scope of impact and meet timelines required under DPDPA for breach reporting or mitigation.
In summary, ShadowMap gives Indian firms “outside-in” visibility—looking at how the world sees their data and infrastructure—and is a valuable complement to internal security efforts for DPDPA compliance.
5. Tenable — Exposure Management & Broad Vulnerability / Attack Surface Coverage
What Tenable offers
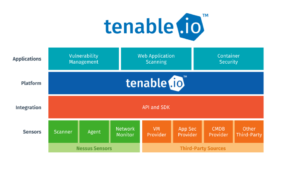
-
Tenable is a leading platform for vulnerability management, risk exposure management, cloud security, attack surface visibility, and threat analytics, under its “Tenable One” umbrella.
-
It extends beyond traditional scanning: Tenable includes modules for external attack surface management (EASM), cloud security posture, identity exposure, OT/IoT risk, and unified exposure analytics.
-
Tenable also integrates with other security tools, supports continuous agent/agentless scanning, and allows organizations to prioritize exposures based on business magnitude and exploitability.
How this helps Indian firms under DPDPA / DPDP
-
Holistic exposure view: Because DPDPA requires safeguarding personal data across environments (on-prem, cloud, apps), Tenable gives a unified view of where exposures lie—helping firms see weak points across infrastructure, cloud, identity, and OT surfaces.
-
Prioritized remediation: Tenable’s analytics help rank vulnerabilities by their real risk to the business (accounting for exploitability, asset criticality), which helps organizations allocate scarce security resources where they matter most.
-
Attack surface coverage: The EASM module can find unknown or forgotten internet-facing assets, which may inadvertently host personal data or APIs—a key concern under DPDPA.
-
Scalability and continuous monitoring: Tenable’s platform supports continuous scanning and integration, ensuring that new vulnerabilities are detected quickly and addressed in time.
-
Compliance readiness & reporting: Its dashboards and reports help mapping exposures against controls, benchmarks, standards, and compliance frameworks, aiding audit and regulatory submissions.
-
Ecosystem synergy: Since Tenable supports integrations (and is compared vs. Qualys in industry comparisons), it can function as a central exposure engine that feeds into governance / privacy platforms (e.g. feeding vulnerabilities into OneTrust or risk dashboards). Tenable®+1
-
Defensible security posture: In case of breaches, Tenable’s data around discovered vulnerabilities, patch history, and exposure trends can support a firm’s position in demonstrating they followed “reasonable security practices” under DPDPA.
Because Tenable is broadly adopted and rich in coverage, Indian organizations can lean on it to secure, monitor, and align with DPDPA’s technical mandates.
8. Toward a Compliance Ecosystem
Putting It All Together: A Suggested Compliance Ecosystem
Here’s how an Indian company might stitch together these vendors/tools into a DPDPA-compliance ecosystem:
| Phase / Function | Role of Vendor / Tool | Benefit & Justification |
|---|---|---|
| Initial Assessment & Audit | TÜV SÜD | Run a DPDPA gap audit, map data flows, identify weaknesses, and produce a compliance roadmap. |
| Privacy Program & Consent / Governance | OneTrust (or GoTrust) | Implement consent management, data inventory, subject rights workflows, rule enforcement, and governance dashboards. |
| Vulnerability Detection & Scanning | Qualys, Tenable | Detect weaknesses in IT, network, cloud, web apps, and infrastructure. Ensure continuous coverage. |
| Risk Enrichment & Remediation Orchestration | Strobes (with Qualys) | Clean up scan noise, correlate issues, prioritize, automate remediation workflows, track fixes. |
| External Exposure & Leak Monitoring | ShadowMap (Security Brigade) | Monitor dark web, leaked credentials, exposed assets, phishing, and external risk signals. |
| Ongoing Monitoring & Maintenance | Tenable / OneTrust / TÜV SÜD | Continuously track exposures, feed insights to governance module, schedule periodic audits, response readiness. |
In essence:
-
TÜV SÜD anchors your compliance program with third-party credibility and structured audits.
-
OneTrust / GoTrust acts as the privacy control plane, enforcing policies, managing consents and rights.
-
Qualys + Strobes bring depth and clarity in vulnerability detection and remediation.
-
ShadowMap extends visibility outward, catching leaks, external exposures, and brand risk.
-
Tenable offers a unified exposure backbone to tie together scanning, context, and prioritization across all domains.
Together, these tools address both the “privacy first” requirements of DPDPA (consent, data mapping, rights, policy) and the “security backbone” requirements (technical safeguards, threat detection, remediation, monitoring).
9. Conclusion
The DPDPA represents both a challenge and an opportunity for Indian enterprises. Compliance cannot be achieved solely through legal teams or security tools; it requires cross-functional alignment, guided by audits, powered by governance platforms, and secured by technical safeguards.
My reflections from the DPO Club event reaffirm that the companies highlighted—TÜV SÜD, OneTrust, GoTrust, Strobes, Qualys, Security Brigade, and Tenable—constitute the backbone of India’s emerging compliance ecosystem. Organizations that adopt such integrated approaches will not only comply with the law but also gain a strategic advantage in trust, credibility, and digital resilience.
References
-
Anderson, C., & Agarwal, R. (2019). The trust benefits of information security certification. MIS Quarterly, 43(2), 525–550.
-
Cavoukian, A. (2010). Privacy by design: The 7 foundational principles. Information and Privacy Commissioner of Ontario.
-
CISA. (2022). Cybersecurity and Infrastructure Security Agency: Exposure management frameworks. U.S. Government Publication.
-
Dragoni, N., Giazzi, F., et al. (2017). Microservices: Yesterday, today, and tomorrow. Springer Ulterior Software Engineering.
-
PwC India. (2023). India’s data protection landscape. PwC Insights.
-
Shostack, A. (2019). Threat modeling: Designing for security. Wiley.
-
Solove, D. (2020). The myth of the privacy paradox. George Washington Law Review, 89(1), 1–48.
-
Voigt, P., & Von dem Bussche, A. (2017). The EU General Data Protection Regulation (GDPR): A practical guide. Springer.
FAQs
1. What is the main goal of the DPDPA in India?
The Act ensures that personal data is collected, processed, and stored responsibly, giving individuals greater rights over their information.
2. How does DPDPA differ from GDPR?
While both share core privacy principles, GDPR has global jurisdiction, whereas DPDPA is tailored to India’s digital economy.
3. Do small businesses also need to comply with DPDPA?
Yes. Even small enterprises handling personal data must comply, though some obligations may be lighter.
4. Which technologies are most critical for compliance?
Audits (TÜV SÜD), governance platforms (OneTrust/GoTrust), vulnerability management (Qualys, Tenable, Strobes), and exposure monitoring (ShadowMap).
5. What are the penalties for non-compliance?
Fines can be substantial, with penalties running into hundreds of crores, depending on the nature of the violation.







